Fintech Innovation – the need for collaboration
Season 2, episode 2
Listen to the full episode here.
Whilst the fintech movement often makes headlines with those firms that are trying to replace traditional financial institutions, there are many more fintech firms out there trying to work, collaborate or sell to those incumbents to help them deliver better outcomes to their customers.
In this podcast we discuss the opportunities for increased collaboration and some of the challenges? Has the pandemic changed the state of play and what are the solutions to accelerate fintech adoption by historical brands?
This podcast will also be an opportunity to announce the launch of the fintech innovation forum at Phoenix.
Guests:
Josif Grace – CEO at Legado
Kevin Spence – Director Financial Services, Scotland & Client Partner
Andy Young – Group Head of Digital & UX at Phoenix Group
Mars mission technology can improve team meetings for introverts
Recruiting a cognitively diverse workforce is essential for productivity, creativity and innovation. People who think differently, however, also prefer to communicate differently in the workplace, too. Introverts, for example, typically prefer to take time to think before contributing. Introverts think to talk whereas extroverts talk to think. So in a normal meeting, whether virtual or face to face, the microphone will tend to be dominated by the more extroverted team members and most of the good ideas from the more introverted team members will be lost.
Our approach to this problem has been to create a workplace collaboration tool for remote meetings using technology developed for astronauts in future deep space exploration missions, successfully tested with NASA and the UK space agency.
Mars is always at least 150 times further away than the Moon and sometimes over 1,000 times further away. The distances are so vast that the radio waves or lasers which will carry the signals will take many minutes to cross the void. The delay will vary with distance but for a crew on Mars it will always be over 3 minutes one-way delay and sometimes over 20 minutes.
The delay cannot be reduced – that is set by the laws of physics – but by splitting dialog into different threads, or braids, and presenting them in a novel way we can make it feel to spaceflight crew and mission control that they are communicating normally.
Using the novel structure and rhythm required for effective remote communication in deep space also produces the opportunity for a new way of interacting during team meetings on Earth. Every participant has an exactly equal chance to contribute to the discussion. Lessons learned from developing human deep space communication technology have the potential to redesign workplace practices to be more inclusive for introverts and other groups, delivering better, more effective, meetings, benefitting the whole team and broader organisation.
For more information, please visit braided.space
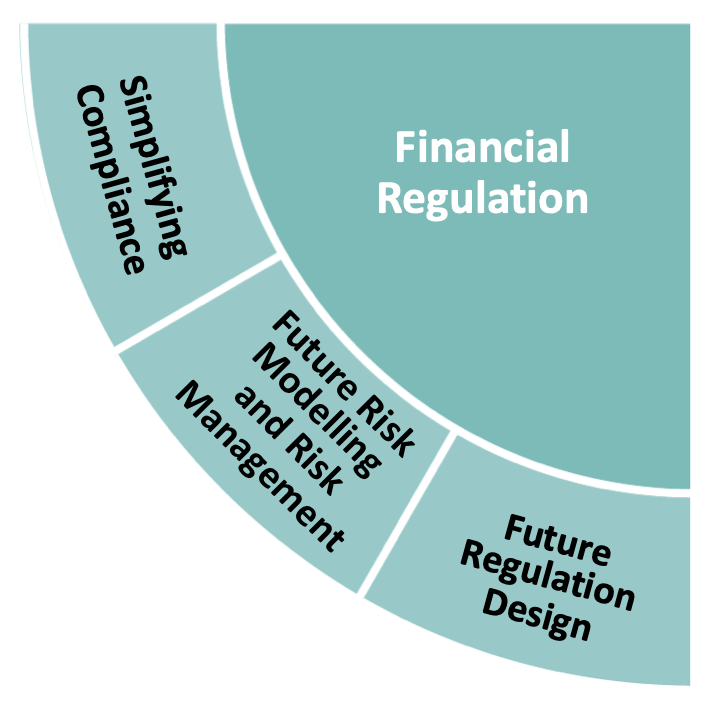
Financial Regulation ”“ the opportunity for FinTech Research & Innovation
The UK’s approach to financial regulation has been key in enabling a dynamic financial services sector that supports and drives the economy, enables a progressive economic outlook, creates jobs, and plays a significant role as a global financial service centre.
The development of this Roadmap highlighted financial regulation as a priority theme because of its fundamental role in FinTech and financial services, as well as the need for financial regulation to support the positive role FinTech innovation could play in the future of finance.
Regulation remains extremely complex for all those operating in the finance industry. Depending on the complexity of the financial institution’s business model, meeting compliance obligations can mean significant costs.
Industry research suggests that some of the largest global financial institutions are spending up to 5% of revenue on regulatory compliance. Across the UK this could mean the annual cost of demonstrating regulatory compliance is as much as £6.6 billion.
Throughout the development of the Roadmap, contributors highlighted their interest in the role technologies could play in future financial regulation. Some examples are AI, advanced analytics, high performance computing including quantum computing, and distributed ledger technologies.
Priority areas in Financial Regulation
The industry contributors to this roadmap offered a view that the future looks set for significantly more change. Our analysis highlighted three topics of interest:
Simplifying compliance
Helping financial institutions create new solutions and use FinTech to help meet current, continuously changing, and global regulatory obligations.
Future risk modelling and risk management
Reinventing risk management with technology and data analytics, and enabling new approaches to fight financial crime, address fraud and focus on emerging climate risks.
- Reinventing risk management with technology and data analytics
- Enabling new approaches to address fraud and fight financial crime
- Modelling for new and emerging climate risks
Future regulation design
Enabling an agile regulatory framework that works for all, and developing future regulatory oversight or supervisory technology.
- Regulatory reporting
- Interoperability and data standardisation
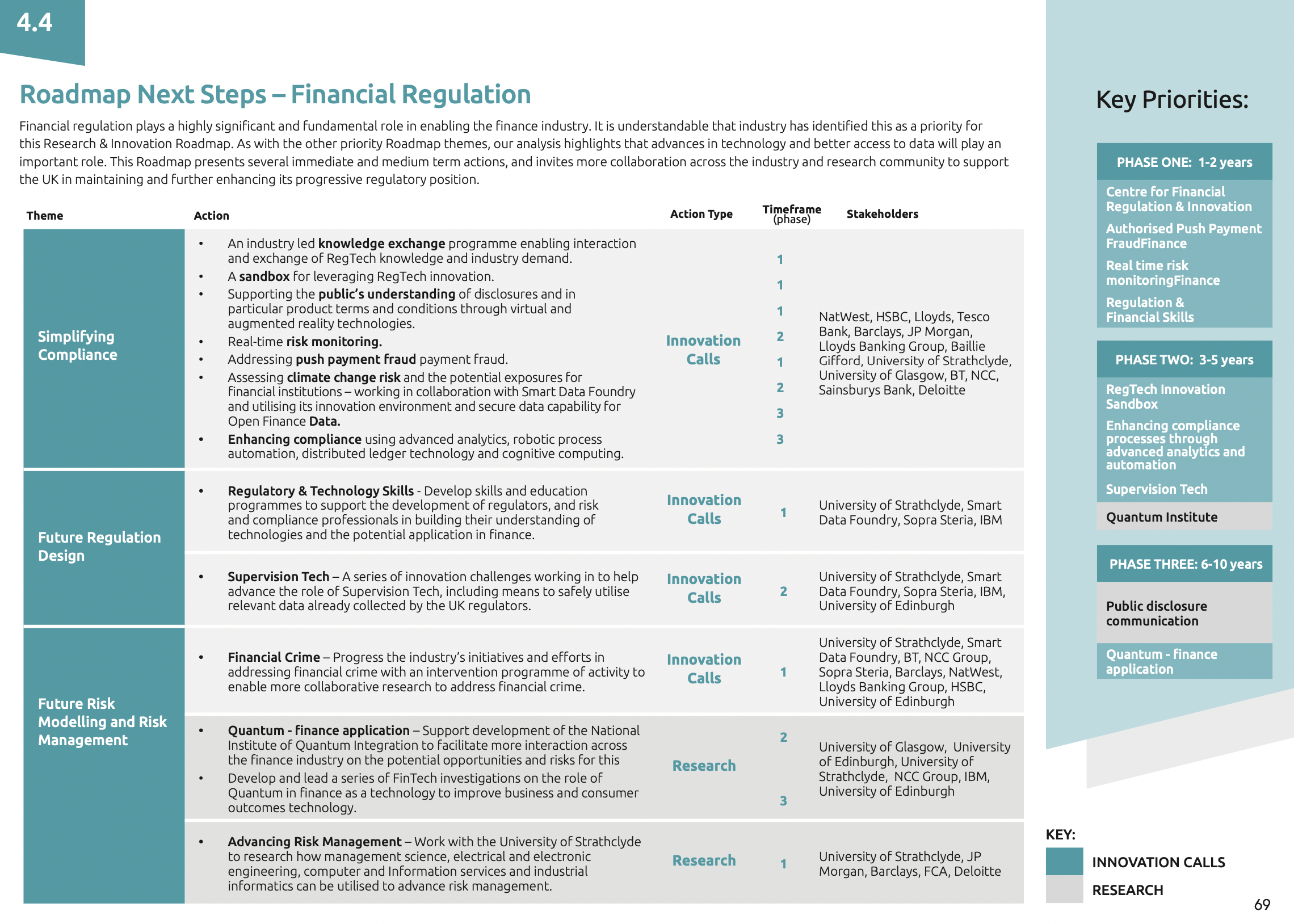
Roadmap next steps: Financial Regulation
A range of proposed next steps are laid out in the published Roadmap, which specifically identifies 13 actions relating to Financial Regulation, and categorises each into one of three phases over the next 10 years. These actions are illustrated in the graphic below. The report also references 23 different stakeholders who can support the implementation of these actions, which are broken down into research projects and innovation calls.
More information about FinTech Scotland’s Research & Innovation Roadmap can be found here, where the full Roadmap can also be downloaded.
The Identity Tooling Needed for Institutional Adoption of DeFi
Blog written by Kai Jun Eer, founder of fintech Onboard ID
In the past year, the term Web3 has become an increasingly used buzzword. The growth in different blockchain protocols and metaverse projects seem to have shed a light on how the new Web3 might look like. We are on the forefront of technology innovation, and we are really excited about it. Yet, it is important to remember that Web3 is not just about crypto and metaverse, but how we define a more user-centric internet. Behind every shining DeFi protocol or NFT project, there is an infrastructural layer supporting them.
Most of the current decentralised finance (DeFi) protocols are pseudonymous in nature (meaning each user is tied to an identifier but not to its real world identity). As these protocols start to grow into institutional adoption, inevitably they will need to comply with certain institutional regulations. One example being some of the users might now need to undergo the Know-Your-Customer (KYC) verification in order to continue interacting with these institutions through the DeFi protocols. I envision that as DeFi matures, the underlying protocol that facilitates the settlement / transactions would be fully decentralised and trustless, while specific use cases can be built on top of the protocol where some might introduce regulations.
A concrete example is Aave, one of the largest DeFi protocols deployed on multiple blockchains such as Ethereum and Avalanche. Aave first started out as a decentralised lending and borrowing protocol. Earlier this year, Aave launched a permissioned protocol (Aave Arc) that targets institutional adoption. The benefits that a blockchain can bring to speed up efficiency of financial settlements do not have to be limited to a fully decentralised setting. However, users that interact with Aave Arc have to undergo KYC in order to meet regulatory requirements.
As more DeFi protocols are becoming more regulated to expand their markets to financial institutions, does that mean that as an end user, each time I want to access a different protocol, I have to undergo a KYC verification again and again? Other than not user-friendly, it makes an already high barrier to entry in DeFi even less accessible.
A digital identity might help. Imagine if an end user only has to undergo the KYC process once, where it receives a digital identity which can be subsequently presented to the different DeFi protocols. With increasing awareness of data privacy and data ownership, users want to be in control of their own data. As an end user, I no longer want to delegate my identity data to a centralised data custodian (think Google ID), especially sensitive data such as what financial services I am accessing. There is a need for a privacy-preserving identity solution, which provides convenience yet still user-centric.
At Onboard ID, we are building the next generation identity tooling, where users are always in control of their own data. Once a user has undergone the usual KYC verification, it receives a cryptographic digital credential which contains the user’s verified identity data. The identity data is only stored in the user’s mobile phone and not in any central databases. An identifier of the credential is recorded on a public permissionless blockchain, such that when the user presents its credential, it is verifiable that the identity data in the credential comes from the trusted KYC provider. The reason our solution is user-centric is that during KYC reverification, data transfer only happens between the user and the verifier without passing through any third parties, not even us as the infrastructure provider. Therefore, users are always in control of how they want to share these data and with whom.
We are currently in beta testing. If your organisation is looking to get an edge in streamlining KYC reverifications, whether it’s in the fintech sector, looking to get into DeFi, or other more specific use cases, please get in touch at kaijuneer@gmail.com! Our vision is to contribute towards building a more user-centric internet, and we hope you could come onboard with us.
Open Banking Reporting joins Visa European Fintech Partner Connect programme
Open Banking Reporting (OBR), a data-driven risk management fintech, has partnered with Visa to enable lenders to provide crucial real time business support.
OBR’s solution OpenRep uses advanced analytics and robotic automation, connecting the SME’s accounting software and banking transactions with commercial credit, Visa and macro-economic data to deliver real time monitoring, proactive alerts, and actionable insights to both the lender and the SME.
OpenRep allows lenders to provide a highly personalised approach to risk assessments through the monitoring of financial trends within a business’ performance; identifying opportunities to support the SME and the insight to act when access to finance is needed most.
Eddie Curran, CEO of Open Banking Reporting, said:
“We are very proud of our flagship product OpenRep and the positive impact it has for both SMEs and lenders.
“By linking real time financial data with advanced analytics and robotic automation we have developed an early-warning system that can help SME owners and lenders identify risks and opportunities. As we continue in a period of economic uncertainty, it is even more important that SMEs and lenders access not just the most up-to-date data, but the tools and technology that turn it into actionable insight.
“OpenRep helps business owners achieve their strategic goals and allows lenders to provide a more proactive and personalised service.”
Through the Fintech Partner Connect Programme Visa will introduce OpenRep to their lending customers firstly in the UK and then into Europe.
Encompass appoints renowned KYC experts
Scotland based fintech Encompass Corporation announced the appointment of senior industry experts to help banks get the benefits of automation initiatives.
The COVID-19 pandemic has accelerated digital transformation. Companies have been eager to reduce onboarding costs and improve customer experience but still need help to build the foundations to achieve this goal.
The newly appointed Transformation Directors will offer practical support and advice that allows Encompass’ customers to drive change and impactful adoption of KYC automation within their organisations.
The new team includes former Barclays senior executive Howard Wimpory who led major global projects, served as a Managing Director within the bank, leading the Group Financial Crime function. He also authored a new whitepaper for Encompass, titled Embracing KYC Transformation’.
Also joining the team, Jo Scanlan, a recognised leader with experience in leading banks Deutsche Bank, HSBC, Macquarie Bank, Westpac and ANZ. She has led global middle office and operations, overseeing a range of areas, including front office and client support, client onboarding, and regulatory compliance and reporting.
Finally, Darren Marion, also joins the team, bringing his experience acquired within several high-profile investment banks, such as UBS, Deutsche Bank, and Citigroup.
Nicola Pickering, VP, Customer Success and Delivery, Encompass, said:
“We are passionate about ensuring that the benefits of investing in our KYC automation are realised by our customers. This requires building partnerships and transformation strategies that encompass people, process, and technology. It has been great to hear directly from customers how valuable our team’s direction and thought leadership has been in navigating KYC transformational change.”
New initiative launched to support fintech in Scotland
FinTech-Tables is an initiative that will bring together the FinTech ecosystem in Scotland to drive growth, innovation, collaboration and connectivity.
Launched by BDM Marketing & Communications and supported by FinTech Scotland, the initiative will deliver a series of events throughout 2022, bringing together the FinTech community in Scotland to discuss and tackle industry-wide challenges in key areas impacting growth including policy and regulation, skills and talent, investment and internationalisation.
Supporting industry priorities, FinTech-Tables will align to the FinTech Scotland Research & Innovation Roadmap 2022-23 which aims to deliver a threefold increase in economic growth and job creation over the next 10 years.
The ambition for the roadmap is to deliver an increase in economic gross value add (GVA) through the FinTech industry in Scotland from £0.5bn today to £21bn GVA by 2031 as well as delivering in excess of 20,000 new FinTech jobs.
FinTech-Tables, which already has support from a number of other organisations including Glasgow based data recruitment specialists MBN Solutions and global payments platform Mambu, will create an environment for the cluster to come together to discuss key findings from the report and create actions to deliver against its objectives, focusing on four priority themes which are considered the building blocks of the roadmap; open finance data, payments & transactions, financial regulation and climate finance.
The forum will launch in May 2022 with its opening event Growing FinTech in Scotland’ and will deliver a series of events and discussions in support of the FinTech industry in Scotland over the next 12 months.
“We’re delighted to support the launch of Fintech Tables. Having recently published the UK Fintech Research and Innovation Roadmap, we believe those events will enable the fintech cluster to meet and discuss many of the findings and actions detailed in the document. We’re looking forward to many interesting conversations with those individuals and companies that make Scotland one of the leading fintech nations”
(Mickael Paris, Marketing Director, FinTech Scotland)
“We are excited to partner with FinTech-Tables and to assist in the work being done by the team to support the growth of the Fintech sector.
Data driven innovation will form a key component when delivering against the key pillars outlined in the Fintech Scotland Research & Innovation Roadmap and the report highlights the importance of data in delivering positive economic, societal, and environmental outcomes in Scotland.
If we are to achieve the desired goal of 32,000 new jobs for the sector in by 2033, it is important that we come together as a community and consider how we can attract a skilled diverse and inclusive talent pool to Scotland from across the entire globe”
(Michael Young, CEO, MBN Solution)
“FinTech in Scotland is already having a huge impact on the way that individuals and businesses interact with money and financial services. It has the power to change lives and have a positive impact on both people and the planet.
Fintech-Tables is committed to supporting the growth of FinTech Scotland. We will do this by creating a community where people can come together to tackle industry issues in an environment that encourages new innovations and partnerships to emerge”
(Ian Davey, Director, BDM Marketing & Communications and Founder of FinTech-Tables)
Protecting your tech startup against Conti type ransomware
Blog written by Alex Jessop, Managing Security Consultant (CIRT) at NCC Group
Background
March saw a 53% increase in ransomware attacks on February, continuing the upward trend for 2022. Conti were the second most prolific group, responsible for 27.52% of the ransomware attacks occurring worldwide[1]. FS-ISAC, in their “Navigating Cyber 2022” report, stated that with the observed trends over recent years, ransomware will remain a top cyber threat to financial institutions[2].
Conti are just another in a long line of Advanced Persistent Threat (APT) actor groups that are targeting organisations for monetary gain. While their arsenal may have some custom tooling, the majority of the Tactics, Techniques and Procedures (TTPs) are well known and used by multiple APT groups. A large proportion of incidents observed by NCC Group would have easily been prevented if policies had been followed or proactive measures taken to understand weaknesses in the environment.
Taking the following three steps will drastically reduce the likelihood of a successful compromise:
- Robust patch management policy
- The majority of initial access vectors observed in Conti attacks would be mitigated
- Enforcing principle of least privilege[3]
- Restricting user permissions would reduce the likelihood of post-exploitation if initial access is gained
- Restricting internet access on servers
- Connectivity is key to threat actors and would make a compromise substantially more difficult if the server estate could not communicate openly with the internet
Executive Summary
In February 2022, a Twitter account which uses the handle ContiLeaks’, started to publicly release information for the operations of the cybercrime group behind Conti ransomware. The leaked data included private conversations between members along with source code methods of delivery. Furthermore, even though the leaks appeared to have a focus on the people behind the Conti operations, the leaked data confirmed (at least to the public domain) that the Conti operators are part of the group, which operates under the TheTrick’ ecosystem. For the past few months, there was a common misconception that Conti was a different entity.
Despite the public disclosure of their arsenal, it appears that Conti operators continue their business as usual by proceeding to compromise networks, exfiltrating data and finally deploying their ransomware. The aim of this article is to describe the methods and techniques we observed during recent incidents that took place after the leaked data.
Our findings can be summarised as below:
- Multiple different initial access vectors have been observed.
- The operator(s) use service accounts of the victim’s Antivirus product in order to laterally move through the estate and deploy the ransomware.
- After getting access, the operator(s) attempted to remove the installed Antivirus product.
- To achieve persistence in the compromised hosts (maintain access), multiple techniques were observed;
- Service created for the execution of Cobalt Strike.
- Multiple legitimate remote access software tools found. These include AnyDesk’, Splashtop’ and Atera’.
- Local admin account Crackenn’ created. (Note: This has been previously reported by Truesec as a Conti behaviour[4])
- Before starting the ransomware activity, the operators are known to have exfiltrated data from the network with the legitimate software Rclone’[5].
It should be noted that the threat actor(s) might use different tools or techniques in some stages of the compromise.
Initial Access
Multiple initial access vectors have been observed recently; phishing emails and the exploitation of Microsoft Exchange servers. The phishing email which was delivered to an employer proceeded to download and install malware which gave the threat actor direct access to the host.
The targeting of Microsoft Exchange saw ProxyShell and ProxyLogon vulnerabilities exploited. This gave threat actors direct access to the Exchange servers. When this vector was observed, the compromise of the Exchange servers often took place two to three months prior to the post exploitation phase.
Other initial access vectors utilised by the Conti operator(s) are:
- Credential brute-force
- Use of publicly available exploits. We have observed the following exploits being used:
- FortiGate VPN
- Log4Shell
- Phishing e-mail sent by a legitimate compromised account, including email accounts of trusted partners
Discovery and Lateral Movement
Once a threat actor has gained access to a host on the network, the threat actor deploys tooling or executes Windows commands to identify hosts on the estate and potential pathways to their objectives.
Typically they begin with network scanning tools to build a picture of the estate and identify what is accessible from the host they currently have access to. Next they will use Windows domain discovery tools to identify users on the domain, as well as user groups which will assist in escalating their privileges .
Lateral movement is usually performed by either:
- Use of Remote Desktop Protocol (RDP) to log onto hosts remotely
- Access across open network shares to copy and execute malware
This phase often occurs within hours or days of initial access being gained.
Persistence
The threat actor leveraged Windows Services to add persistence for the Cobalt Strike beacon. Cobalt Strike is a popular tool for adversary simulation and was the main command and control framework utilised by this group.
In addition, services were also installed to provide persistence for the Remote Access Tools deployed by the threat actor:
- AnyDesk
- Splashtop
- Atera
Local accounts have also been created by the threat actor on patient zero to maintain access.
Privilege Escalation
Conti operator(s) managed to escalate their privileges by compromising and using different accounts that were found in the compromised host. The compromised credentials in engagements undertaken by NCC were found to be compromised through the use of tools such as Mimikatz, which is a well-known tool to extract credentials from running processes.
One operator was also observed exploiting ZeroLogon to obtain credentials and move laterally.
Exfiltration and Encryption
Similar to many other threat actors, Conti operator(s) exfiltrate a large amount of data from the compromised network using the legitimate software Rclone’. Rclone’ is a legitimate file transfer tool which is used to manage files on cloud storage or a private file server. When cloud storage is used, Mega is the option chosen by this group.
Soon after the data exfiltration, the threat actor(s) started the data encryption. In addition, we estimate that the average time between the lateral movement and encryption is five days.
As discussed previously, the average dwell time of a Conti compromise is heavily dependant on the initial access method. Those incidents that have involved ProxyShell and ProxyLogon, the time between initial access and lateral movement has been three to six months. However once lateral movement is conducted, time to completing their objective is a matter of days.
Recommendations
- Monitor firewalls for traffic categorised as filesharing
- Monitor firewalls for anomalous spikes in data leaving the network
- Patch externally facing services immediately
- Monitor installed software for remote access tools
- Restrict RDP and SMB access between hosts
- Implement a Robust Password Policy[6]
- Provide regular security awareness training
References
- https://www.mynewsdesk.com/nccgroup/news/ncc-group-monthly-threat-pulse-march-2022-446743
- https://www.fsisac.com/navigatingcyber2022-report?utm_campaign=2022-GIOReport&utm_source=media&utm_medium=PressRelease
- https://docs.microsoft.com/en-us/windows-server/identity/ad-ds/plan/security-best-practices/implementing-least-privilege-administrative-models
- https://www.truesec.com/hub/blog/proxyshell-qbot-and-conti-ransomware-combined-in-a-series-of-cyber-attacks
- https://research.nccgroup.com/2021/05/27/detecting-rclone-an-effective-tool-for-exfiltration/
- https://www.ncsc.gov.uk/collection/passwords/updating-your-approach
Photo by Tima Miroshnichenko: https://www.pexels.com/photo/people-typing-on-keyboards-5380596/
AG Elevate launches accelerator programme
Addleshaw Goddard just launched its 5th AG Elevate programme ”“ an accelerator for those looking to become the next tech-unicorn.
This fast-track 10-month programme is designed to accelerate the growth of tech businesses in all sectors of the economy helping them with legal challenges that can arise as they grow.
Previous AG Elevate cohorts have included Scottish fintechs Amiqus, Trace and OBR.
The programme is designed, developed and delivered by AG‘s expert lawyers, who will provide access to legal advice, legal and business mentors and networks across the globe.
Elvan Hussein, Partner and co-programme lead at Addleshaw Goddard, said:
“We have emerged from the pandemic into a different environment, with tech integrated in all aspects of our lives and this continues to both offer opportunities for high growth and the chance for tech businesses to play a huge part in rebuilding and growing our economies wherever they are based.”
“AG Elevate is tried and tested and we understand what matters most to these businesses, and what challenges they will inevitably face. Our mentors have the specialist sector knowledge to bring tangible added value to the relationships with their Elevate members, beyond their undoubted legal expertise and we can’t wait to meet our new cohort.”
To qualify for consideration for a place on the programme, businesses need to have existing plans for high–growth and have received external funding.
Interested parties can apply at www.addleshawgoddard.com/en/
Encompass named ”˜RegTech Partner of the Year’
Scotland-based Encompass won RegTech Partner of the Year’ at this year’s British Bank Awards.
Now in its eighth year, the awards, run by Smart Money People, recognise top financial products and innovation based on more than 81,000 votes.
This recognition comes after Encompass was selected as a category finalist in both 2021 and 2020.
Wayne Johnson, CEO and co-founder of Encompass, said:
We’re thrilled, and proud, to have been named as RegTech Partner of the Year at this year’s British Bank Awards.
Being chosen as the overall winner among such strong competition demonstrates not only our impact across the banking sector, but also the loyalty of our customers, who voted for us.
2022 is shaping up to be a strong year for our business globally, and we have big plans for growth in the months ahead, as we continue to work with and for our expanding customer base.
Jacqueline Dewey, CEO of Smart Money People, added:
With the awards 100% voted for by consumers and no judging panel, the British Bank Awards truly reflect the best of the UK banking industry, and the commitment and engagement these organisations have from their customers.
This year, our winners range from the newest firms in the market to well-established household names, illustrating the breadth and depth of the UK’s financial services market across many sectors. We’re absolutely delighted for our winners but also hope that these awards serve a higher purpose in helping consumers and businesses make more informed choices about who they trust with their hard-earned money.