Strong potential for FinTech in the Japanese Market
How does one get Big in Japan? Throughout the years this has puzzled the companies of the west and continues to be relevant in the FinTech space. As a market it presents both a challenge and a great opportunity to FinTechs looking to expand (Deloitte1). In this blog we’ll explore the key features of the Japanese FinTech market.
The Opportunity
First and foremost, Japanese market represents a wealth of potential customers with large cash holdings to be mobilised. According to a recent Reuters article2 Japanese households currently hold over $17 trillion, more than half of which is highly liquid cash or deposits. Japanese corporations are also known for unusually large cash holdings.
In addition, Japan is the third largest economy in the world by GDP and is a stable and highly convenient society. As the outlook for VC and growth capital turns uncertain in western markets, rather than seeking a quick market share and easy profits, a convincing long-term investment into a large and relatively untouched domestic market may look more and more attractive.
Furthermore, Japan is open as an innovation hub3. It is ranked No.1 among G7 countries in R&D expenditure as a percentage of GDP and No.1 in the world in patent applications per million of population. There’s lot going on to facilitate innovation in Japan, such as supporting start-up ecosystems in several cities by the government. The Japanese Government is also keen to promote Japan as an international finance hub4 by assisting asset managers and FinTechs to enter the market. Japan holds incredible excitement and expectation for a world in which technology is highly integrated; the Society 5.0’5 plan is a great example of this.
Challenges
However, to unlock the great potential of the Japanese market there are several barriers that must be surpassed. Most obviously, entry to such a market could be a daunting prospect due to language and cultural barriers. Also, as the Deloitte article highlights the Japanese customer puts great value on quality. To meet high expectations deep market research prior to entry or partnerships with Japanese corporations are highly desirable.
Additionally, Japanese financial institutions and customer habits have historically been somewhat rigid. One of the most prominent examples of this for FinTech companies is the strong reliance on cash. Companies have opted for QR code systems rather than the more convenient contactless NFC solutions. Japan is not a market that simply follows global trends immediately. Winning over the Japanese business community and customers will take time and effort but will be well worth it.
Support for breaking into the market
While these hurdles may seem high the Japanese government has several organisations ready, willing, and able to assist. The first step is to talk to JETRO (Japanese External Trade Organisation). As a government organisation we can provide initial market research, introductions to funding or partner corporations and from there continue to assist should you wish to setup up an entity in Japan, all completely free of charge. There are also incentives from organisations like the Tokyo Metropolitan Government which has been featured on this blog previously6. Once again in 2022 they are holding financial awards competitions in both the Financial Innovation and ESG7 categories.
Beyond the capital
Tokyo, while an attractive hub, is by no means the only option. Focus on regions beyond the capital is an issue that JETRO keeps at the forefront. Two cities to watch in this space are Osaka and Fukuoka, both of which are vying to become financial hubs. Similarly, while JETRO’s UK office is London-based we understand there is so much more to the UK than just London. We look forward to cooperating with Scottish FinTechs that are interested in the Japanese market so don’t hesitate to reach out!
JETRO London Contact:
Author: Roderic Robertson roderic_robertson@jetro.go.jp
Reference List
1https://www2.deloitte.com/jp/en/pages/financial-services/articles/bk/jp-fi-fintech-in-japan.html
2https://www.reuters.com/world/asia-pacific/japan-households-accumulate-record-financial-assets-covid-curbs-spending-2022-03-17/
3https://www.jetro.go.jp/en/invest/investment_environment/whyjapan/ch2.html
4https://www.fsa.go.jp/en/financialcenter/financialcenter.html
5https://www8.cao.go.jp/cstp/english/society5_0/index.html
6https://www.fintechscotland.com/next-stop-japan-apply-for-the-tokyo-financial-award-2020/
7https://www.finaward.metro.tokyo.lg.jp/en/
Photo by Aleksandar Pasaric: https://www.pexels.com/photo/people-walking-on-the-streets-surrounded-by-buildings-1510595/
interview with a FinTech intern
who am I?
My name is Jack Barclay, I am an s6 pupil at Portobello High School who is currently working as an intern at FinTech Scotland. I have been given the opportunity to write a short blog post discussing my thoughts and opinions towards the FinTech and tech industry, as well as my aspirations and plans for my internship.
Are you interested in working in tech?
Yes absolutely. Technology is such a huge part of the current landscape and the influence it has will only increase each year and that’s why I’m interested in it. In my mind it is one of the few industries that will only continue to grow, develop and evolve as we use it to solve issues and problems we face in everyday life.
Do you feel curriculums include enough tech subjects?
Yes and no. I feel that when I went to primary (school) the consensus was not one that overwhelmingly supported technology in the learning environment but moving into secondary school the general attitude seemed to have changed. The school (Portobello High School) was incredibly supportive of technology, going as far as to provide an iPad to every pupil. This came with an education too, teaching us how to use a variety of systems and software’s such as the Microsoft family of products (OneNote, teams, PowerPoint and excel.) As well as this we are given the opportunity to study various subjects relating to the technology umbrella, such as computing. I studied computing and the skills taught were quite wide, such as python, html, CSS, and JavaScript. So overall I would say my experience is that schools now more than ever are striving to educate students on technology and get them excited about it at a younger age.
Had you ever heard of FinTech prior to this internship?
Prior to this internship I had not, the whole industry is quite new to me. But I am excited to learn more. And use my existing knowledge to adapt to a new climate, full of unfamiliar problems and new experiences.
What do you think it is about?
Well, the current consensus I am getting is that fintech is an industry full of innovation & collaboration that has one main goal, which is to support growth and evolution of new technologies in the financial sector. I absolutely connect with that.
What skills do you think are needed?
I would imagine one skill that would be useful is problem solving, being able to produce solutions quickly and efficiently to problems you may never have faced before. As well as this I think having an open mind would be incredibly useful, being open to the latest ideas and innovations. Also, collaboration, I think the ability to work in a team is necessary within not just fintech but in the technology sector, the ability to listen to others, give feedback, and evolve ideas as a community is a super useful skill to have.
Do you think your female friends would be interested in a job at fintech?
I would certainly think so, but they probably don’t represent the majority. I imagine the majority wouldn’t, It is an industry overwhelmingly populated by men and does not necessarily market itself toward women. More must be done to advertise the technology sector to girls/women.
Why did you want to get work experience at FinTech Scotland?
Well the team reflected a number of the ideals that I have, And the company’s mission to make a better world for all through innovation, collaboration and inclusion really resonated with me.
What do you hope to learn?
I hope to learn skills that will enhance and develop my ability in the workspace, I want to gain experience from those who are enthusiastic and knowledgeable about the industry. and I want to improve the skills and ability I have by using them and in an atmosphere I have not worked in before. And i
am optimistic about what I can get out of the internship as I have already started learning. Over my first week I learned that there are so many ways to get jobs/roles in this industry. You do not need to spend 4yrs of your life getting a degree, there are other routes, and each route will suit every person differently.
If nothing else I hope this blog post works as a lite introduction into my mind. As well as my skills, abilities, and my ambitions for my time here at FinTech Scotland.
Trevor Jones – a story of art and NFTs
I never planned on or expected to be an artist. Although I took art classes in high school in Canada (as I had a natural talent) it wasn’t until my early 30s that everything changed. I left my home country in my mid-20s with a backpack to explore the world, working mostly in hospitality to get around and ended up in Scotland a few years later on a UK ancestry visa. After making some bad decisions I spiralled into depression, and I hit an important crossroads in life. For some strange reason, I decided that art would save me’.
Proving one’s never too old to follow one’s dreams, I enrolled in a foundation course at a small school in Edinburgh and the following year I was accepted into Edinburgh University and Edinburgh College of Art for the 5 year MA Fine Art programme. Thankfully, I managed to escape the dark depths of depression by the time I graduated; however, I now found myself at 38 years of age, broke and armed with very little but a huge student loan and an art degree.
Moreover, after two moderately successful commercial gallery solo exhibitions, I came to the conclusion that it was near impossible to make a living as an artist. So, there I was, working two jobs; managing a small art charity and teaching part time whilst running an Airbnb year round at my flat, to make ends meet all while spending every other spare moment painting.
I realised that if I were to make my art career dream viable that I would need to somehow differentiate myself from all the other artists exhibiting in Scotland, which led me to exploring and integrating new technologies with my work. In 2011 I was investigating QR code oil paintings and by early 2013 I was employing augmented reality as one of the first professional painters in the world to use AR.
I was more than excited when it came to exploring art and tech innovation but unfortunately it appeared the Scottish art world felt almost the exact opposite to me. As constant rejection of my artworks continued to fuel my frustration with the institutions was mounting, I decided to troll the legacy artworld with various tech inspired stunts.
For example, after my AR painting was rejected once again from the annual Royal Scottish Academy open exhibition, I snuck into the RSA building the day before the opening to photograph all the works on display. That night I augmented over 60 paintings and digitally replaced’ them with my pieces. I counterfeited 25 invitations and turned up to the posh opening night with a bunch of friends with smartphones and tablets and my AR app turning the event into the Trevor Jones solo exhibition. Some of the old guard’ weren’t too happy with me after this stunt but at the same time I also managed to build a little excitement and momentum around my artwork.
Fast forward to 2017 and for once I had a bit of money in the bank after a successful AR solo exhibition ”“ one that I’d organised myself as commercial galleries were no longer interested in showing my paintings. I invested in Bitcoin and very quickly became consumed with the world of crypto. I began coordinating my next solo show, which was titled Crypto Disruption: The Art of Blockchain. Almost all the paintings sold to crypto enthusiasts internationally via bitcoin and eth (which completely boggled my mind at that time!) and it was by far my most successful exhibition.
Near the end of 2019 I dropped my first NFT, a collaboration with the late, great Alotta Money, which broke all previous NFT sales records and really put me on the cryptoart map. I think I was a bit of an anomaly, as an academically trained painter coming into this space filled with almost entirely digital artists; which again, likely helped to differentiate me from the rest.
Things have continued to go from strength to strength with the last couple years being quite literally life changing both creatively and financially. Along with my record breaking Bitcoin Angel open edition drop on Niftygateway, seven figure sales collaborations with Pak, Metacask and the legend Ice Cube, and hiring Stirling Castle in July to throw an exclusive party for 300 of my angel collectors, I’m now working on a commission which will be a gift for a very high profile individual who makes electric cars and rockets.
My dad always used to say to me, “Son, life’s a funny thing” and he wasn’t wrong. I guess I’ll now add to his words with, “Work hard, persevere, focus on being different and you never know where you may end up.”
Why early payments could be the key to strengthening supply chains
Why early payments could be the key to strengthening your supply chain
Having a strong supply chain is one of the most powerful tools you can have in your arsenal. Creating a solid network of all the organisations involved in delivering your product or service to your end customer ”“ from vendors to producers, warehouses to retailers ”“ is critical to keeping things running smoothly. In fact, it can make or break your success.
But if there’s one factor that can help boost and strengthen supply chains, across all sectors and industries, that often gets overlooked, it’s the power of early payments.
Here’s why they could be the key to making your supply chain even stronger.
Building confidence and trust
It might sound simple, but don’t under-estimate the importance of having confidence in and being able to trust each and every member of your supply chain. Early payments can help build this confidence ”“ for both suppliers and customers alike.
If you’re a buyer, offering to pay early (for example in return for a small discount), signifies that you’ve got the cash ready and waiting, and are considerate of the fact that your supplier might benefit from a boost to their cash flow before the date their invoice is due.
For suppliers, being able to incentivise your customers to pay early by offering a small discount signals sound financial wellbeing. If you’re able to offer your services or products at a beneficial cost, it implies you’re not stretched to the last penny ”“ which gives customers confidence and reassurance that you’re not at risk and they’ll be able to keep buying from you.
Access to better deals
It goes without saying that, if early payment benefits both buyer and supplier, there could be great deals attached to paying up early. When either side is empowered to use early payment as a tool for negotiation ”“ whether that’s a reduction in price, a speedier delivery, or another mutually agreed benefit ”“ it can help move things along exponentially, and might even lead to longer term process changes in your supply chain that keep things really efficient and effective.
Reputation builder
If you’re a buyer that’s offering to pay early, you’re going one step further than avoiding a reputation as a nightmare customer that your supplier has to keep chasing: you’ll become a preferred choice.
When suppliers are stretched or at capacity, they’ll be in a position to choose who they work with. Customers or buyers with good reputations for paying on time (or, even better, early) are much more likely to make their way up the food chain of preference ”“ and might even attract more suppliers looking to work with them, as a result of word of mouth, too.
Growth on both sides
It’s no secret that, for the SMEs and start-ups that form a bulk of the UK’s suppliers, cash is king. Offering early payment can be a real cash injection that helps SMEs out with their cashflow. And good cashflow means more money to invest and grow.
But the benefits aren’t one sided. If you’re a buyer that’s looking to grow, you’ll need your suppliers to be able to keep up with your ambitions ”“ which will likely lead to an increased demand for goods or services. By paying them early and helping them grow, you’ll be helping them to help you grow, when the time comes.
Only as strong as your weakest link
When it comes down to it, your supply chain is only as strong as its weakest link ”“ and late payment has a habit of breaking the bonds that the chain relies on. In fact, according to a recent survey of 500 UK decision makers, 86% agreed that one single late payment affects everyone in the supply chain. And, out of the 31% of businesses that admitted paying a supplier late, almost half say it was due to a late or failed payment from their customer.
So, if late payment has a knock-on, negative impact on everyone in a supply chain, imagine the knock-on, positive impact that early payment could have, if things were reversed?
How Early Pay can help
If reading this has convinced you that building early payment into your supply chain is something you should be looking at, you’re in the right place.
Our CEO, Anthony Persse, thinks it’s time to turn the conversation about late payment on its head: “By shifting towards a more positive conversation about early payment’, we will do much more than simply improve payment performance. We will help create more jobs, deliver greater levels of investment and generate deeper social value with long-term sustainability at a time when the country needs it most.”
If you’d like more information visit saltare.io, or please get in touch with the team at Info@saltare.io and we’ll be happy to help.
Mars mission technology can improve team meetings for introverts
Recruiting a cognitively diverse workforce is essential for productivity, creativity and innovation. People who think differently, however, also prefer to communicate differently in the workplace, too. Introverts, for example, typically prefer to take time to think before contributing. Introverts think to talk whereas extroverts talk to think. So in a normal meeting, whether virtual or face to face, the microphone will tend to be dominated by the more extroverted team members and most of the good ideas from the more introverted team members will be lost.
Our approach to this problem has been to create a workplace collaboration tool for remote meetings using technology developed for astronauts in future deep space exploration missions, successfully tested with NASA and the UK space agency.
Mars is always at least 150 times further away than the Moon and sometimes over 1,000 times further away. The distances are so vast that the radio waves or lasers which will carry the signals will take many minutes to cross the void. The delay will vary with distance but for a crew on Mars it will always be over 3 minutes one-way delay and sometimes over 20 minutes.
The delay cannot be reduced – that is set by the laws of physics – but by splitting dialog into different threads, or braids, and presenting them in a novel way we can make it feel to spaceflight crew and mission control that they are communicating normally.
Using the novel structure and rhythm required for effective remote communication in deep space also produces the opportunity for a new way of interacting during team meetings on Earth. Every participant has an exactly equal chance to contribute to the discussion. Lessons learned from developing human deep space communication technology have the potential to redesign workplace practices to be more inclusive for introverts and other groups, delivering better, more effective, meetings, benefitting the whole team and broader organisation.
For more information, please visit braided.space
Financial Regulation ”“ the opportunity for FinTech Research & Innovation
The UK’s approach to financial regulation has been key in enabling a dynamic financial services sector that supports and drives the economy, enables a progressive economic outlook, creates jobs, and plays a significant role as a global financial service centre.
The development of this Roadmap highlighted financial regulation as a priority theme because of its fundamental role in FinTech and financial services, as well as the need for financial regulation to support the positive role FinTech innovation could play in the future of finance.
Regulation remains extremely complex for all those operating in the finance industry. Depending on the complexity of the financial institution’s business model, meeting compliance obligations can mean significant costs.
Industry research suggests that some of the largest global financial institutions are spending up to 5% of revenue on regulatory compliance. Across the UK this could mean the annual cost of demonstrating regulatory compliance is as much as £6.6 billion.
Throughout the development of the Roadmap, contributors highlighted their interest in the role technologies could play in future financial regulation. Some examples are AI, advanced analytics, high performance computing including quantum computing, and distributed ledger technologies.
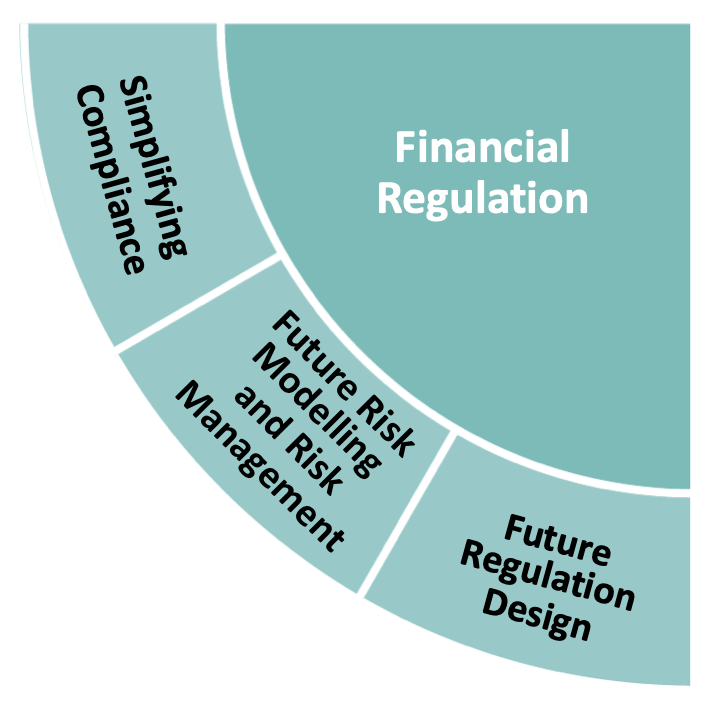
Priority areas in Financial Regulation
The industry contributors to this roadmap offered a view that the future looks set for significantly more change. Our analysis highlighted three topics of interest:
Simplifying compliance
Helping financial institutions create new solutions and use FinTech to help meet current, continuously changing, and global regulatory obligations.
Future risk modelling and risk management
Reinventing risk management with technology and data analytics, and enabling new approaches to fight financial crime, address fraud and focus on emerging climate risks.
- Reinventing risk management with technology and data analytics
- Enabling new approaches to address fraud and fight financial crime
- Modelling for new and emerging climate risks
Future regulation design
Enabling an agile regulatory framework that works for all, and developing future regulatory oversight or supervisory technology.
- Regulatory reporting
- Interoperability and data standardisation
Roadmap next steps: Financial Regulation
A range of proposed next steps are laid out in the published Roadmap, which specifically identifies 13 actions relating to Financial Regulation, and categorises each into one of three phases over the next 10 years. These actions are illustrated in the graphic below. The report also references 23 different stakeholders who can support the implementation of these actions, which are broken down into research projects and innovation calls.
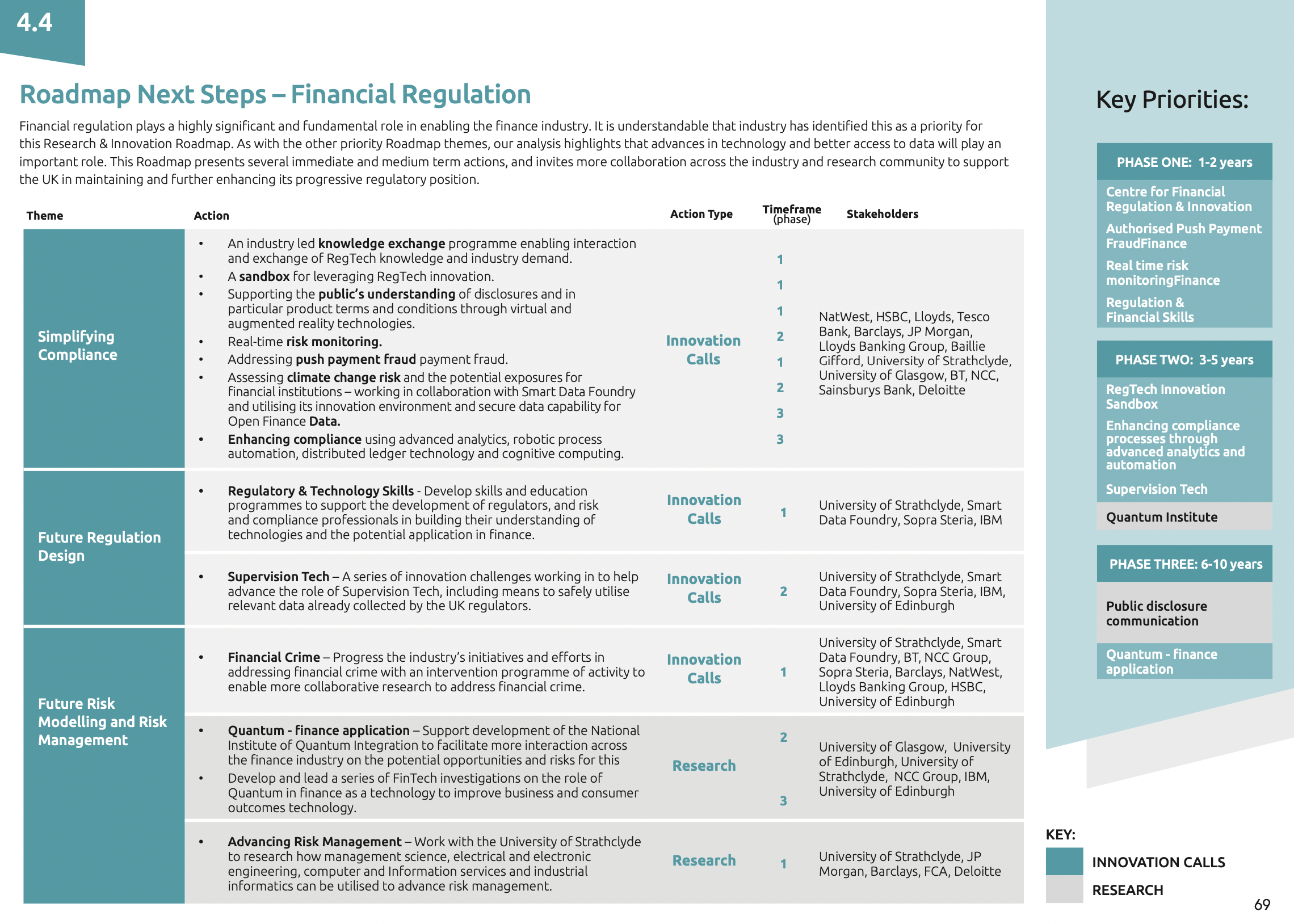
More information about FinTech Scotland’s Research & Innovation Roadmap can be found here, where the full Roadmap can also be downloaded.
The Identity Tooling Needed for Institutional Adoption of DeFi
Blog written by Kai Jun Eer, founder of fintech Onboard ID
In the past year, the term Web3 has become an increasingly used buzzword. The growth in different blockchain protocols and metaverse projects seem to have shed a light on how the new Web3 might look like. We are on the forefront of technology innovation, and we are really excited about it. Yet, it is important to remember that Web3 is not just about crypto and metaverse, but how we define a more user-centric internet. Behind every shining DeFi protocol or NFT project, there is an infrastructural layer supporting them.
Most of the current decentralised finance (DeFi) protocols are pseudonymous in nature (meaning each user is tied to an identifier but not to its real world identity). As these protocols start to grow into institutional adoption, inevitably they will need to comply with certain institutional regulations. One example being some of the users might now need to undergo the Know-Your-Customer (KYC) verification in order to continue interacting with these institutions through the DeFi protocols. I envision that as DeFi matures, the underlying protocol that facilitates the settlement / transactions would be fully decentralised and trustless, while specific use cases can be built on top of the protocol where some might introduce regulations.
A concrete example is Aave, one of the largest DeFi protocols deployed on multiple blockchains such as Ethereum and Avalanche. Aave first started out as a decentralised lending and borrowing protocol. Earlier this year, Aave launched a permissioned protocol (Aave Arc) that targets institutional adoption. The benefits that a blockchain can bring to speed up efficiency of financial settlements do not have to be limited to a fully decentralised setting. However, users that interact with Aave Arc have to undergo KYC in order to meet regulatory requirements.
As more DeFi protocols are becoming more regulated to expand their markets to financial institutions, does that mean that as an end user, each time I want to access a different protocol, I have to undergo a KYC verification again and again? Other than not user-friendly, it makes an already high barrier to entry in DeFi even less accessible.
A digital identity might help. Imagine if an end user only has to undergo the KYC process once, where it receives a digital identity which can be subsequently presented to the different DeFi protocols. With increasing awareness of data privacy and data ownership, users want to be in control of their own data. As an end user, I no longer want to delegate my identity data to a centralised data custodian (think Google ID), especially sensitive data such as what financial services I am accessing. There is a need for a privacy-preserving identity solution, which provides convenience yet still user-centric.
At Onboard ID, we are building the next generation identity tooling, where users are always in control of their own data. Once a user has undergone the usual KYC verification, it receives a cryptographic digital credential which contains the user’s verified identity data. The identity data is only stored in the user’s mobile phone and not in any central databases. An identifier of the credential is recorded on a public permissionless blockchain, such that when the user presents its credential, it is verifiable that the identity data in the credential comes from the trusted KYC provider. The reason our solution is user-centric is that during KYC reverification, data transfer only happens between the user and the verifier without passing through any third parties, not even us as the infrastructure provider. Therefore, users are always in control of how they want to share these data and with whom.
We are currently in beta testing. If your organisation is looking to get an edge in streamlining KYC reverifications, whether it’s in the fintech sector, looking to get into DeFi, or other more specific use cases, please get in touch at kaijuneer@gmail.com! Our vision is to contribute towards building a more user-centric internet, and we hope you could come onboard with us.
Protecting your tech startup against Conti type ransomware
Blog written by Alex Jessop, Managing Security Consultant (CIRT) at NCC Group
Background
March saw a 53% increase in ransomware attacks on February, continuing the upward trend for 2022. Conti were the second most prolific group, responsible for 27.52% of the ransomware attacks occurring worldwide[1]. FS-ISAC, in their “Navigating Cyber 2022” report, stated that with the observed trends over recent years, ransomware will remain a top cyber threat to financial institutions[2].
Conti are just another in a long line of Advanced Persistent Threat (APT) actor groups that are targeting organisations for monetary gain. While their arsenal may have some custom tooling, the majority of the Tactics, Techniques and Procedures (TTPs) are well known and used by multiple APT groups. A large proportion of incidents observed by NCC Group would have easily been prevented if policies had been followed or proactive measures taken to understand weaknesses in the environment.
Taking the following three steps will drastically reduce the likelihood of a successful compromise:
- Robust patch management policy
- The majority of initial access vectors observed in Conti attacks would be mitigated
- Enforcing principle of least privilege[3]
- Restricting user permissions would reduce the likelihood of post-exploitation if initial access is gained
- Restricting internet access on servers
- Connectivity is key to threat actors and would make a compromise substantially more difficult if the server estate could not communicate openly with the internet
Executive Summary
In February 2022, a Twitter account which uses the handle ContiLeaks’, started to publicly release information for the operations of the cybercrime group behind Conti ransomware. The leaked data included private conversations between members along with source code methods of delivery. Furthermore, even though the leaks appeared to have a focus on the people behind the Conti operations, the leaked data confirmed (at least to the public domain) that the Conti operators are part of the group, which operates under the TheTrick’ ecosystem. For the past few months, there was a common misconception that Conti was a different entity.
Despite the public disclosure of their arsenal, it appears that Conti operators continue their business as usual by proceeding to compromise networks, exfiltrating data and finally deploying their ransomware. The aim of this article is to describe the methods and techniques we observed during recent incidents that took place after the leaked data.
Our findings can be summarised as below:
- Multiple different initial access vectors have been observed.
- The operator(s) use service accounts of the victim’s Antivirus product in order to laterally move through the estate and deploy the ransomware.
- After getting access, the operator(s) attempted to remove the installed Antivirus product.
- To achieve persistence in the compromised hosts (maintain access), multiple techniques were observed;
- Service created for the execution of Cobalt Strike.
- Multiple legitimate remote access software tools found. These include AnyDesk’, Splashtop’ and Atera’.
- Local admin account Crackenn’ created. (Note: This has been previously reported by Truesec as a Conti behaviour[4])
- Before starting the ransomware activity, the operators are known to have exfiltrated data from the network with the legitimate software Rclone’[5].
It should be noted that the threat actor(s) might use different tools or techniques in some stages of the compromise.
Initial Access
Multiple initial access vectors have been observed recently; phishing emails and the exploitation of Microsoft Exchange servers. The phishing email which was delivered to an employer proceeded to download and install malware which gave the threat actor direct access to the host.
The targeting of Microsoft Exchange saw ProxyShell and ProxyLogon vulnerabilities exploited. This gave threat actors direct access to the Exchange servers. When this vector was observed, the compromise of the Exchange servers often took place two to three months prior to the post exploitation phase.
Other initial access vectors utilised by the Conti operator(s) are:
- Credential brute-force
- Use of publicly available exploits. We have observed the following exploits being used:
- FortiGate VPN
- Log4Shell
- Phishing e-mail sent by a legitimate compromised account, including email accounts of trusted partners
Discovery and Lateral Movement
Once a threat actor has gained access to a host on the network, the threat actor deploys tooling or executes Windows commands to identify hosts on the estate and potential pathways to their objectives.
Typically they begin with network scanning tools to build a picture of the estate and identify what is accessible from the host they currently have access to. Next they will use Windows domain discovery tools to identify users on the domain, as well as user groups which will assist in escalating their privileges .
Lateral movement is usually performed by either:
- Use of Remote Desktop Protocol (RDP) to log onto hosts remotely
- Access across open network shares to copy and execute malware
This phase often occurs within hours or days of initial access being gained.
Persistence
The threat actor leveraged Windows Services to add persistence for the Cobalt Strike beacon. Cobalt Strike is a popular tool for adversary simulation and was the main command and control framework utilised by this group.
In addition, services were also installed to provide persistence for the Remote Access Tools deployed by the threat actor:
- AnyDesk
- Splashtop
- Atera
Local accounts have also been created by the threat actor on patient zero to maintain access.
Privilege Escalation
Conti operator(s) managed to escalate their privileges by compromising and using different accounts that were found in the compromised host. The compromised credentials in engagements undertaken by NCC were found to be compromised through the use of tools such as Mimikatz, which is a well-known tool to extract credentials from running processes.
One operator was also observed exploiting ZeroLogon to obtain credentials and move laterally.
Exfiltration and Encryption
Similar to many other threat actors, Conti operator(s) exfiltrate a large amount of data from the compromised network using the legitimate software Rclone’. Rclone’ is a legitimate file transfer tool which is used to manage files on cloud storage or a private file server. When cloud storage is used, Mega is the option chosen by this group.
Soon after the data exfiltration, the threat actor(s) started the data encryption. In addition, we estimate that the average time between the lateral movement and encryption is five days.
As discussed previously, the average dwell time of a Conti compromise is heavily dependant on the initial access method. Those incidents that have involved ProxyShell and ProxyLogon, the time between initial access and lateral movement has been three to six months. However once lateral movement is conducted, time to completing their objective is a matter of days.
Recommendations
- Monitor firewalls for traffic categorised as filesharing
- Monitor firewalls for anomalous spikes in data leaving the network
- Patch externally facing services immediately
- Monitor installed software for remote access tools
- Restrict RDP and SMB access between hosts
- Implement a Robust Password Policy[6]
- Provide regular security awareness training
References
- https://www.mynewsdesk.com/nccgroup/news/ncc-group-monthly-threat-pulse-march-2022-446743
- https://www.fsisac.com/navigatingcyber2022-report?utm_campaign=2022-GIOReport&utm_source=media&utm_medium=PressRelease
- https://docs.microsoft.com/en-us/windows-server/identity/ad-ds/plan/security-best-practices/implementing-least-privilege-administrative-models
- https://www.truesec.com/hub/blog/proxyshell-qbot-and-conti-ransomware-combined-in-a-series-of-cyber-attacks
- https://research.nccgroup.com/2021/05/27/detecting-rclone-an-effective-tool-for-exfiltration/
- https://www.ncsc.gov.uk/collection/passwords/updating-your-approach
Photo by Tima Miroshnichenko: https://www.pexels.com/photo/people-typing-on-keyboards-5380596/
Payments & Transactions, the fintech opportunity
 is discussing the key outputs in a series of blogs. This blog focuses on Payments & Transactions, which is one of the four key strategic priority themes.
is discussing the key outputs in a series of blogs. This blog focuses on Payments & Transactions, which is one of the four key strategic priority themes.
The way we pay for things is changing. Throughout the development of the Research & Innovation Roadmap, payments and transactions were referred to in the broad context of the transfer of value (either money, goods, or assets) in exchange for goods and services.
The Roadmap pinpoints the significant move from physical exchanges to digital transactions, and identifies several significant trends that could mean payments will change significantly in years to come. These changes will have a significant impact on the economy, and could also have a substantial impact on citizens and businesses, which is why the future of payments is one of the four priority themes identified.
The importance of Payments & Transactions
The pandemic accelerated the move from physical to digital in many aspects of our lives, including how we make transactions. Customers’ digital expectations and a shift towards more instant electronic payments are having a significant impact on our economy, and a new digital economy is emerging strongly, with major implications for consumers and SMEs alike.
Across the development of the Roadmap, when looking at the theme of the future payments we considered the topic of digital currencies and crypto currencies. These innovations present new ways for value to be stored and exchanged. It is clear there is a still a lot to learn about the potential, the impact, and the implications of cryptocurrencies as a method for mainstream payments. Stablecoin is a form of cryptocurrency that is linked to an asset that is stable in value, and stablecoins are generating significant interest for future payments and value exchange.
The UK Government has established a crypto assets taskforce, and the UK regulators are considering the benefits and risks on a range of issues connected to this topic, including a separate digital currency backed by a central bank. Since the publication of the Roadmap, HM Treasury has confirmed its commitment to the development of appropriate regulation for crypto.
As we further explored the payments theme, we identified technologies of particular interest, such as AI, blockchain and distributed ledger tools. Industry expressed interest about how these technologies could offer a completely different way to organise and manage payment systems, providing a route to real-time, cross-border payments worldwide. These developments pave the way for a potentially very different future of value exchange. According to the World Economic Forum, up to 10% of global GDP could be stored on blockchains by 2025.
Embedded payments is one of the hottest topics in FinTech in 2022, and was another area of particular focus. Technology is advancing the methods to embed payments in everyday experiences and allow customers and businesses to pay for purchases without entering bank details, credit, or debit card information.
Historically, the payments process has lived at the edges of experience for businesses. Payments were either taken in cash, or offline, with no real lasting insights into the customer and the goods or services they purchased. Technology businesses are now fully embedding software that enables a change to this experience, creating more choice and allowing businesses to have a deeper connection with customers. In addition to high profile examples such as Uber, many embedded payment innovations are emerging, such as in-car payments, smart fridges and connected homes.
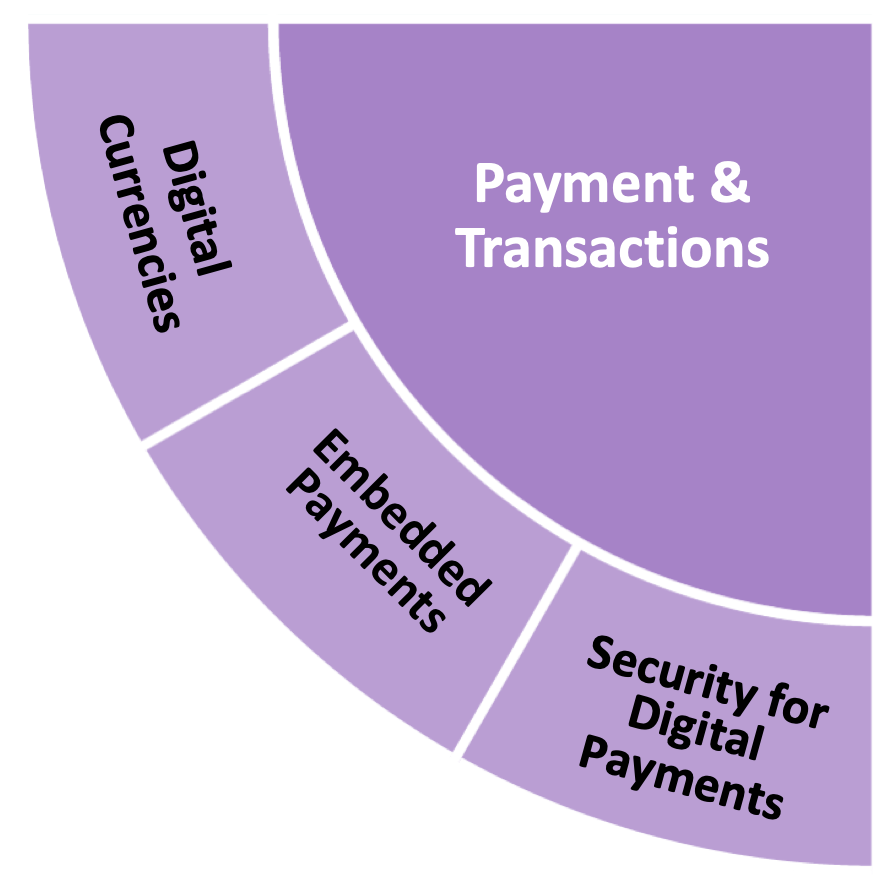
Priority areas in Payments & Transactions
The industry contributors to this roadmap offered a view that the future looks set for significantly more change. Our analysis highlighted three topics of interest:
Digital currencies
- Cryptocurrencies and stablecoins
- Distributed ledger technology
Embedded payments
- SME market
- Retail consumers
Security for digital payments
- Cyber security
- Biometrics
Roadmap next steps: Payments & Transactions
A range of proposed next steps are laid out in the published Roadmap, which specifically identifies 10 actions relating to Payments & Transactions, and categorises each into one of three phases over the next 10 years. These actions are illustrated in the graphic below. The report also references 23 different stakeholders who can support the implementation of these actions, which are broken down into research projects and innovation calls.
More information about FinTech Scotland’s Research & Innovation Roadmap can be found here, where the full Roadmap can also be downloaded.
MyIdentity and Improving Identity Verification
Department for Digital, Culture, Media and Sport (DCMS) and the Digital Identity & Attributes Trust Framework (DIATF)
The Government wants to improve how digital identity is done and demonstrate what a good’ digital identity should look like. As such, the DCMS has made a number of commitments to create a framework for what a good digital identity should look like. They will establish a Governance function to own these rules and make sure that they are followed and develop proposals to remove legislative and regulatory blockers’ for the use of secure identities, whilst ensuring the protection of citizens.
Underneath the DIATF are a number of identity schemes. Each aligned to the DCMS Framework and working to ensure interoperability, as each scheme will have their own nuances to meet the specific needs of its sector.
Etive have been working on the design and development of a scheme for the home buying and selling process since 2018, followed by two rounds of public funding, first from Scottish Enterprise and then Innovate UK.
Is there a problem with identity in the home buying and selling process?
The home buying and selling process is a long transaction built on trust between relying parties – estate agents, conveyancers, brokers and lenders. Each is regulated differently and works to often competing standards and consequently each is not allowed to trust and rely on the identity verification (IDV) carried out by the other.
This has resulted in consumers having to prove their identity up to 5 times through the process, often using different information at different times. This causes great frustration, friction and cost for consumers, as well as relying parties. As one consumer responded, ID checks are currently a joke, I have provided 12 different forms of ID and problems with them all’.
We should also not forget that due to events since 2020, with less face-to-face interactions, there is a greater reliance on digital IDV methods and property and mortgage fraud continues to rise.
MyIdentity Trust Scheme & Regulations
The solution is the development of a trust scheme enabling a consumer to get the IDV done once, which they own, and can share to all relying parties.
The MyIdentity scheme is based on the principles of the DCMS Framework and the Good Practice Guide 45 (GPG45; How to prove and verify someone’s identity). To ensure compliance with Anti-Money Laundering (AML) and compliance for firms, AML regulations were updated in 2019 enabling firms to use an IDV carried out by a certified third party so long as ”¦it is accredited or certified to offer the identity verification service through a governmental or industry process that involved meeting minimum published standards’.
These third parties are identity service providers (IDSPs) and since January 2022 approximately 45 organisations are going the DCMS certification process. Liability has also shifted onto these IDSPs.
Financial Services and MyIdentity
The MyIdentity scheme is participating in the FCA’s regulatory sandbox, enabling firms to test innovative offerings in a live environment and provides FCA regulated firms with the protections that they need to embrace the Government and MyIdentity standards.
MyIdentity is also working through UK Finance to work to get MyIdentity into a position that lenders will accept a MyIdentity IDV and how financial organisations can re-use these IDV’s for all financial services, a re-usable identity, a DCMS objective.
Further work is being done to help remove the blockers for other cohorts involved in the sales process such as conveyancers and brokers who rely on the lender’s handbooks’ from both UK Finance and the Building Societies Association (BSA).
MyIdentity Outcomes
The Beta stage of the project is testing processes and technology looking at improved IDV standards, regulation of providers and greater protections for consumers and the industry.
If we look at Norway, for example, when they developed their trust network, BankID, fraud reduced from 2% of financial transactions to 0.00042% and mortgage lending times reduced to 1 day.
Great work is being done by the industry, coming together, to help improve the process of home buying and selling, also a policy objective of The Department for Levelling Up, Housing and Communities (DLUCH).